「CV」 数字水印资源汇总
在不影响数字载体(包括多媒体——图片、视频、音频,文档,软件等)使用价值的情况下,将标识信息嵌入到载体中;
数字水印侧重于水印信息的鲁棒性,隐写侧重中水印信息的隐蔽性;
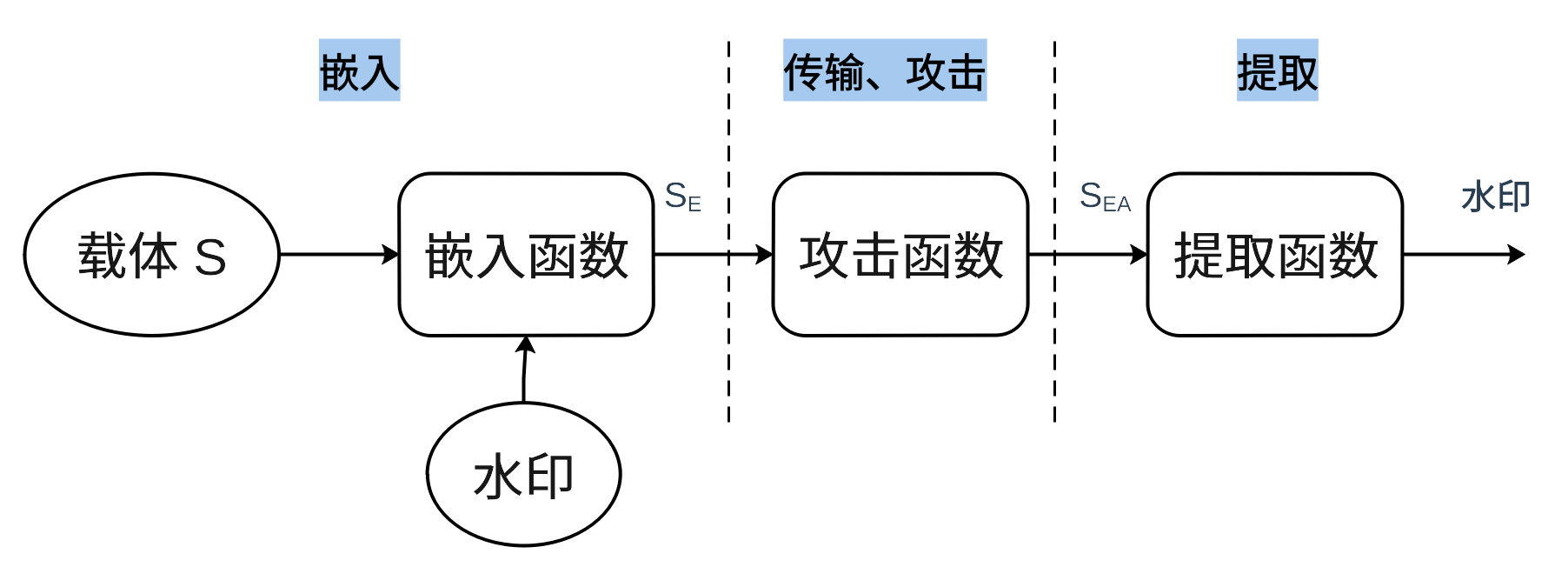
图1:数字水印流程
Digital Watermarking · Steganography
1 数字水印
1.1 综述
-
Watermarking of Digital Images
2012-06-03 paper
$\bullet \bullet$
关于传统算法的水印综述,内容非常全面广泛,除了没有覆盖到 DL;
貌似是 99 年的论文,因为原稿丢了,12 年重新出版了这个; - A Survey of Digital Watermarking Techniques and its Applications
2014-07-17 paper
$\bullet \bullet$ 入门
关于传统水印算法的总数,总共 4 页,真是短小精悍;看完会对水印有个整体认识的,非常推荐作为水印入门读物;可惜了我花了两天时间要死要活地折腾出一个Survey,要是早看到这篇,分分钟搞定,看来还是综述文章最容易入门;
- Analysis of Visible and Invisible Image Watermarking – A Review
2016-08 paper
针对传统方法的综述,主讲了 DWT、DCT 和 DFT;文章内容较少,不是一篇优质的 review,应该是频域水印算法回顾;
- A Comprehensive Survey of Watermarking Relational Databases Research
2018-01-25 paper
数据库和数字指纹综述;似乎已经超出 CV 领域,不过也有借鉴意义,空了可以看;
1.2 理论
- Steganography Security: Principle and Practice
2018-06-10 paper
对比了隐写术和数字水印的安全性差异;
1.3 传统方法
-
A New Method For Digital Watermarking Based on Combination of DCT and PCA
TELFOR 2014 2015-09-10 paper -
Digital image watermarking using normal matrices
2015-05-23 paper -
OR-Benchmark: An Open and Reconfigurable Digital Watermarking Benchmarking Framework
2015-05-31 paper
1.4 深度学习
1.4.1 通用
-
Watermarking Deep Neural Networks for Embedded Systems
ICCAD 2018 2018 paper -
Turning Your Weakness Into a Strength: Watermarking Deep Neural Networks by Backdooring
2018-02-13 paper -
Protecting Intellectual Property of Deep Neural Networks with Watermarking
AsiaCCS 2018 paper -
On the Robustness of the Backdoor-based Watermarking in Deep Neural Networks
2019-06-18 paper
1.4.2 图像
1.4.3 音频
1.4.4 视频
1.4.5 网络模型
给模型打水印;
-
DeepSigns: An End-to-End Watermarking Framework for Protecting the Ownership of Deep Neural Networks
paper -
Embedding Watermarks into Deep Neural Networks
ICMR 2017 2017-01-15 paper | keras -
Digital Watermarking for Deep Neural Networks
2018-02-06 paper -
Have You Stolen My Model? Evasion Attacks Against Deep Neural Network Watermarking Techniques
2018-09-03 paper -
Cryptographic key distribution over a public network via variance-based watermarking in compressive measurements
2019-03-30 paper -
Effectiveness of Distillation Attack and Countermeasure on Neural Network Watermarking
2019-06-14 paper
1.4.6 跨模态
2 隐写术
1.1 综述
-
Deep Learning in steganography and steganalysis from 2015 to 2018
2019-03-31 paper -
Recent Advances of Image Steganography with Generative Adversarial Networks
2019-06-18 paper
GAN 在隐写术里的应用;
2.2 理论
- Steganography Security: Principle and Practice
2018-06-10 paper
对比了隐写术和数字水印的安全性差异;
2.3 传统方法
2.4 深度学习
2.4.1 通用
-
Moving Steganography and Steganalysis from the Laboratory into the Real World
2013-06-20 paper
显示应用; -
SSGAN: Secure Steganography Based on Generative Adversarial Networks
2017-06-06 paper -
Convolutional Neural Network Steganalysis’s Application to Steganography
2017-11-06 paper -
Generative Steganography with Kerckhoffs’ Principle based on Generative Adversarial Networks
2017-11-14 paper -
CycleGAN, a Master of Steganography
NIPS 2017 2017-12-08 paper -
SteganoGAN: High Capacity Image Steganography with GANs
2019-01-12 paper | pytorch-offical | 文档 -
Learning Symmetric and Asymmetric Steganography via Adversarial Training
2019-03-13 paper -
BASN – Learning Steganography with Binary Attention Mechanism
2019-07-09 paper -
Steganography using a 3 player game
2019-07-14 paper
2.4.2 图像
-
Generating steganographic images via adversarial training
2017-03-01 paper -
End-to-end Trained CNN Encode-Decoder Networks for Image Steganography
2017-11-20 paper -
A Novel Convolutional Neural Network for Image Steganalysis with Shared Normalization
2017-11-20 paper -
Deep Learning Hierarchical Representations for Image Steganalysis
2017-11 paper | pytorch -
CNN Based Adversarial Embedding with Minimum Alteration for Image Steganography
IEEE 2018-03-24 paper -
Spatial Image Steganography Based on Generative Adversarial Network
2018-04-21 paper -
StegNet: Mega Image Steganography Capacity with Deep Convolutional Network
2018-06-17 paper | tensorflow-offical -
Invisible Steganography via Generative Adversarial Networks
2018-07-23 paper -
Efficient feature learning and multi-size image steganalysis based on CNN
2018-07-30 paper
ZhuNet,任意尺寸输入,Inception 有效性证明; -
StegoAppDB: a Steganography Apps Forensics Image Database
2019-04-19 paper
数据集; -
EncryptGAN: Image Steganography with Domain Transform
2019-05-28 paper
2.4.3 音频
-
Steganography between Silence Intervals of Audio in Video Content Using Chaotic Maps
2016-10-14 paper
音轨中静默片段放水印; -
StegIbiza: Steganography in Club Music Implemented in Python
2017-05-22 paper -
AAG-Stega: Automatic Audio Generation-based Steganography
AAAi 2019 2018-09-10 paper -
Hide and Speak: Deep Neural Networks for Speech Steganography
2019-02-07 paper -
Heard More Than Heard: An Audio Steganography Method Based on GAN
2019-07-11 paper
2.4.4 视频
2.4.5 网络模型
给模型打水印;
- DeepStego: Protecting Intellectual Property of Deep Neural Networks by Steganography
2019-03-05 paper
2.4.6 跨模态
3 攻击
-
Fraternal Twins: Unifying Attacks on Machine Learning and Digital Watermarking
2017-03-16 paper -
Attacks on Digital Watermarks for Deep Neural Networks
2019 paper
4 防篡改
video tampering
-
Computer-Aided Annotation for Video Tampering Dataset of Forensic Research
2018-02-07 paper -
ARCHANGEL: Tamper-proofing Video Archives using Temporal Content Hashes on the Blockchain
CVPR 2019 workshop 2019-04-26 paper
附录
A 参考资料
B 数据集
| 数据集 | 训练集(万张) | 验证集(万张) | 测试集(万张) | 分辨率 |
|---|---|---|---|---|
| BOSS | 0.9 | 0.1 | 512×512 |
Comments